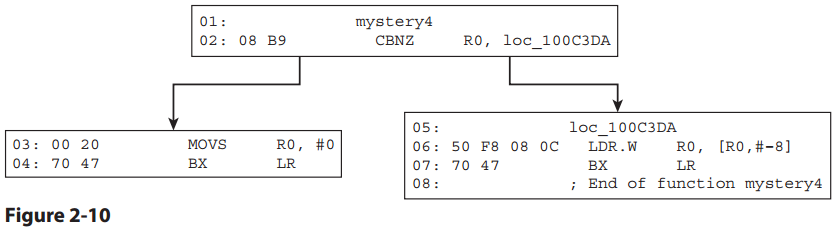
Figure 2-10 shows another easy function.
Here is the function's disassembly:
 |
| Figure 2-10. Practical Reverse Engineering. © 2014 by Bruce Dang |
The ARM processor is in Thumb state. This function takes a pointer of an unknown type. If the pointer is null, it returns 0. Otherwise it subtracts 8 bytes from the pointer and returns the value there.
DWORD sub8_ptr(void *r0)
{
/* CBNZ R0, loc_100C3DA */
if (r0 == NULL)
return 0; /* MOVS R0, #0 */
return *(r0 - 8); /* LDR.W R0, [R0,#–8] */
}
No comments :
Post a Comment